Configure ANAF OAuth 2.0 secrets
Any application that communicates with ANAF, including your app, requires an authorization step. Therefore, you must configure your app’s ANAF OAuth 2.0 secrets if you would like to use any of the following services:
“Secrets” refer to the following:
- Client ID - the unique identifier of your app in its relationship with ANAF.
- Client secret - a secret code that you obtain from ANAF which authorizes your app to consume ANAF services.
- Callback URL - a URL designated by you to which ANAF should send the results of the OAuth 2.0 authorization attempt.
There are two configuration approaches that you may choose from:
- Let SBS manage the ANAF secrets for your app. If you choose this option, you do not not need to set up a developer account with ANAF and register your app with ANAF. Instead, your app’s ANAF credentials will be managed by SBS. This option is easier to set up but it may not be suitable if you need greater control over the ANAF authorization process (for example, if you would like to implement a custom GUI for your app’s users to authorize with ANAF and need a custom callback URL). With this approach, your app will not have its own OAuth 2.0 client ID and client secret in its communication with ANAF but will use the implicit ones provided by SBS.
- Set up your own app’s credentials with ANAF, and then enter them into SBS. This approach lets you have precise control over every aspect of the OAuth 2.0 authorization with ANAF. Namely, your app will use its own client ID and client secret in its communication with ANAF. Also, you can designate a custom callback URL to which ANAF should respond after an authorization attempt.
Use SBS-managed ANAF secrets
If you would like to opt in for SBS-managed (implicit) ANAF secrets:
- In the SBS Console, run the
updateAppmutation and set theroAnafEfacturaUseImplicitClientSecretorroAnafEtransportUseImplicitClientSecretflags to true.
mutation updateApp ($id:ID!,$input:UpdateAppInput!) {
updateApp(id:$id, input:$input) {
id
name
active
createdAt
roAnafEfacturaClientSecret { clientId clientSecret oauthCallback }
roAnafEfacturaUseTestEnvironment
roAnafEfacturaUseImplicitClientSecret
roAnafEtransportClientSecret { clientId clientSecret oauthCallback }
roAnafEtransportUseTestEnvironment
roAnafEtransportUseImplicitClientSecret
}
}
In the variables, make sure to replace YOUR_APP_ID with the actual id of your app in SBS.
{
"id": "YOUR_APPLICATION_ID",
"input": {
"roAnafEfacturaUseImplicitClientSecret": true,
"roAnafEtransportUseImplicitClientSecret": true
}
}
Note that, as long as the ANAF secrets are implicit, the field clientSecret, when querying the app’s details, will always return the value null. In other words, it is not possible to see the implicit client secret for either E-Transport or E-Factura, which is intentional.
Set up custom ANAF OAuth 2.0 credentials
If you choose this option, the configuration steps are as follows:
- On ANAF website (https://anaf.ro), create an API developer account, see Creating an ANAF API developer account. If you already have an ANAF API developer account, you may omit this step.
- From your ANAF API developer account, register your application for OAuth. As a result of registering your application, you will obtain a set of RO ANAF credentials (client ID, client secret). For details, see Registering an OAuth application with ANAF.
- From the SBS Console (or programmatically from the Accounts API), you must update your app with the RO ANAF credentials obtained previously. For details, see Updating your app’s ANAF OAuth 2.0 credentials.
Creating an ANAF API developer account
To create a new ANAF API developer account:
- Open the ANAF home page, https://anaf.ro.
- Navigate to Servicii Online > Înregistrare utilizatori > Dezvoltatori aplicații > Înregistrare pentru API-uri, and fill in the required fields.
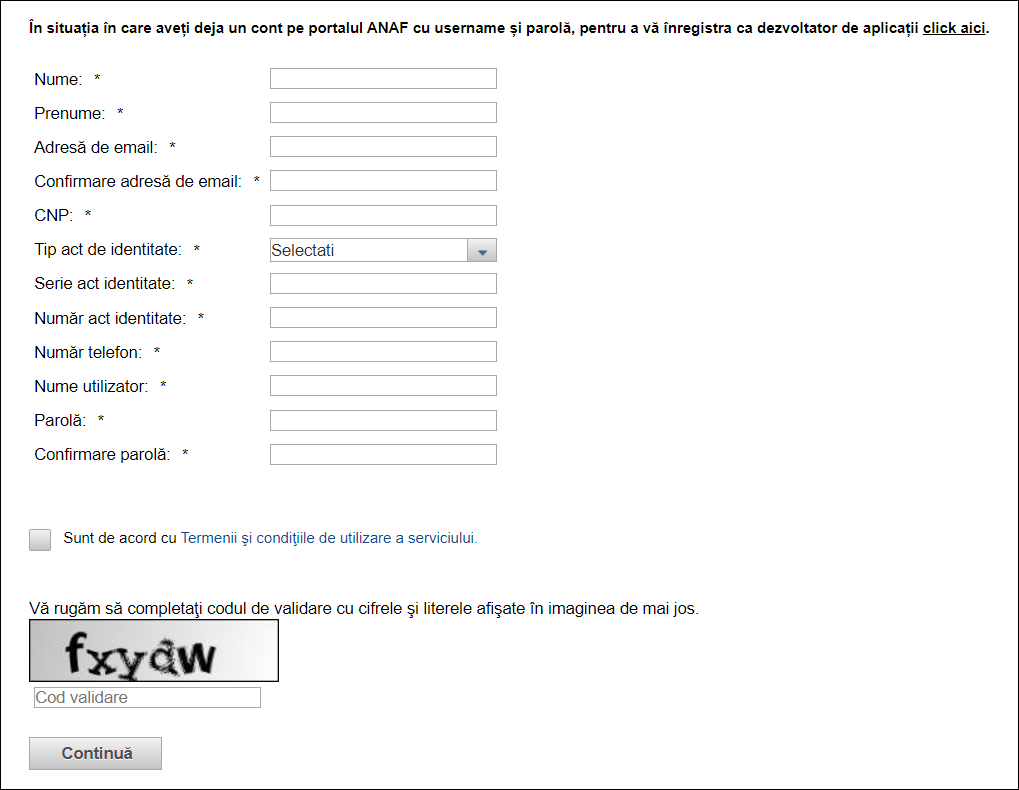
- Click Continuă. Shortly afterwards, you will receive an email message with an activation URL.
- Open the received URL to activate your ANAF API developer account.
Registering an OAuth application with ANAF
Once you have created the ANAF API developer account as outlined above, take the following steps to register your OAuth application:
-
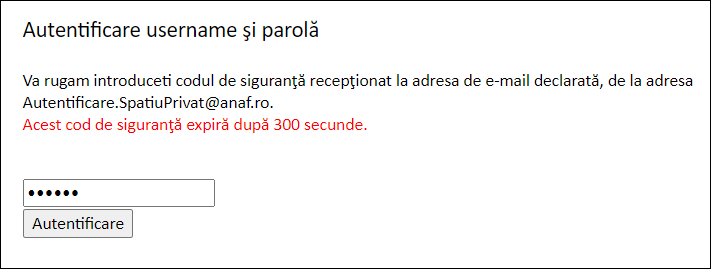
On https://www.anaf.ro, click Autentificare utilizator and enter your ANAF API developer credentials.
-
Click Autentificare. An access code should now be sent to your email address.
-
Enter the received code and click Autentificare again.
-
Click Editare profil OAuth.
-
Fill in the fields as follows:
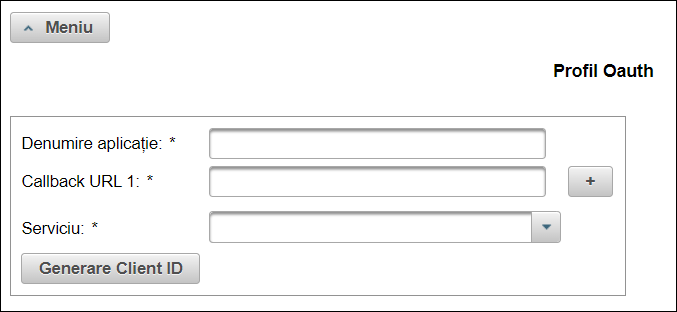
Denumire aplicatie The name of your app. This field must not contain spaces. Callback URL 1 This is the URL at which ANAF will return the outcome of the authorization process after your app’s user has gone through it. Note that the chosen callback URL directly affects your implementation, as further described under Applications with a Web interface and Applications with a desktop interface. If your application does not have a Web interface, you can enter the default callback URL https://ro-anaf-oauth-api.socrate.io/oauth-callback.Serviciu Select E-Transport, E-Factura, or both, depending on what services your app needs to integrate with. For increased security, you may want to create a new app (and thus obtain a new set of client ID/client secret) for each of the services individually. -
Click Generare Client ID and be patient while the page loads. On success, a client ID and client secret will be generated for your app and displayed on the page. You will subsequently need to enter this information into SBS; make sure to keep it secret.
Updating your app’s ANAF OAuth 2.0 credentials
After registering your application for OAuth with ANAF, you obtain a client ID and a client secret. These credentials must be entered, along with the callback URL, into SBS. This enables your SBS app to authorize users with ANAF and obtain ANAF tokens (access and refresh tokens) required to consume the RO E-Transport and RO E-Factura services.
To update your SBS app with ANAF credentials:
- In the SBS Console, run the
updateAppmutation and provide the OAuth credentials obtained from ANAF as parameters.
The following code listing illustrates updating both the E-Factura and E-Transport credentials.
mutation update_app($id: ID!, $input: UpdateAppInput!) {
updateApp(id: $id, input: $input) {
roAnafEfacturaClientSecret{
clientId
clientSecret
oauthCallback
},
roAnafEtransportClientSecret{
clientId
clientSecret
oauthCallback
}
}
}
Make sure to replace variables with the values generated on the ANAF OAuth page. You may use the same client ID and client secret for both if, on the ANAF OAuth page, you generated a single client ID and client secret for both E-Transport and E-Factura.
{
"id":"YOUR_APPLICATION_ID",
"input": {
"roAnafEfacturaClientSecret": {
"clientId": "YOUR_ANAF_CLIENT_ID",
"clientSecret": "YOUR_ANAF_CLIENT_SECRET",
"oauthCallback": "YOUR_CALLBACK_URL"
},
"roAnafEtransportClientSecret": {
"clientId": "YOUR_ANAF_CLIENT_ID",
"clientSecret": "YOUR_ANAF_CLIENT_SECRET",
"oauthCallback": "YOUR_CALLBACK_URL"
}
}
}
Note
The roAnafEfacturaUseImplicitClientSecret and roAnafEtransportUseImplicitClientSecret flags must be either false or null. If they are true, your app uses implicit credentials, see Use SBS-managed ANAF secrets.
Managing additional ANAF OAuth 2.0 secrets
In the most simple scenario, an app uses a single OAuth 2.0 callback URL for both e-Factura and e-Transport. This callback URL is stored at app level in the roAnafEfacturaClientSecret and roAnafEtransportClientSecret settings, respectively. As already mentioned, you can configure this callback URL to be either the implicit one (provided by SBS), or a custom URL of your choice. In either case, any ANAF authorization request from any tenant linked to the current app will use the respective callback URL and its associated secrets (client ID, client secret) during the ANAF authorization process. This is the most common usage scenario and it is typically sufficient for most business cases.
Should you need, however, to have multiple custom ANAF OAuth callback URLs for your app, this is possible by configuring the so-called additional ANAF client secrets for e-Factura and e-Transport. The additional client secrets are stored in the roAnafEfacturaAdditionalClientSecrets and roAnafEtransportAdditionalClientSecrets attributes of your application. These attributes of array type and so can accommodate as many additional callback URLs as required. Each object in the array has three attributes:
clientIdclientSecretoauthCallback
You can enter these values by updating your application. All three values should be provided exactly as obtained from the ANAF OAuth portal, as described above.
The following code listing shows how to update an existing app with additional ANAF OAuth 2.0 secrets:
mutation updateApp($id:ID!,$input:UpdateAppInput!) {
updateApp(id:$id, input:$input) {
id
name
roAnafEfacturaAdditionalClientSecrets { clientId clientSecret oauthCallback }
roAnafEtransportAdditionalClientSecrets { clientId clientSecret oauthCallback }
}
}
{
"id": "YOUR_APPLICATION_ID",
"input": {
"roAnafEfacturaAdditionalClientSecrets": [
{
"clientId": "YOUR_ANAF_CLIENT_ID",
"clientSecret": "YOUR_ANAF_CLIENT_SECRET",
"oauthCallback": "YOUR_OAUTH_CALLBACK_URL"
}
],
"roAnafEtransportAdditionalClientSecrets": [
{
"clientId": "YOUR_ANAF_CLIENT_ID",
"clientSecret": "YOUR_ANAF_CLIENT_SECRET",
"oauthCallback": "YOUR_OAUTH_CALLBACK_URL"
}
]
}
}
Additional callback URLs and client secrets work as follows:
- When you run the
generateAuthorizationRequestof the RO ANAF OAuth 2.0 Service, you can optionally supply an input parameter calledoauthCallbackto the mutation. If you set this parameter to any of the callback URLs that are present inroAnafEfacturaAdditionalClientSecretsorroAnafEtransportAdditionalClientSecrets, then the respective callback URL and its associated client secrets will be used for the ANAF authorization. When the authorization expires, the respective set of secrets will also be used to obtain the refresh token from ANAF. - SBS will also check if the
oauthCallbacksupplied as parameter is present in the “main” setting (that is, inroAnafEtransportClientSecretorroAnafEfacturaClientSecret). If it is, then the “main” client secret and callback URL defined inroAnafEtransportClientSecretorroAnafEfacturaClientSecretwill be used for the ANAF authorization. - If you don’t supply the
oauthCallbackparameter at all, then the “main” client secret and callback URL defined inroAnafEtransportClientSecretorroAnafEfacturaClientSecretwill be used for the ANAF authorization.