Configure Azure OAuth 2.0 secrets
You must configure your app’s Azure OAuth 2.0 secrets in the following cases:
- You would like to use the User Management Service to authenticate users into your app with their existing Microsoft Account.
- You would like to use the Email Service in order to let your app’s users to connect their Microsoft-managed inbox to the app, for sending email directly from the app. For details about this scenario, see Sending email from a Google or Microsoft 365 email address.
Before you proceed, register your new app in Azure and configure it for OAuth 2.0, as described in Configure an Azure App.
Updating your app’s Azure OAuth 2.0 secrets
-
Sign in to the Azure portal (https://azure.microsoft.com) and navigate to “App Registrations”.
-
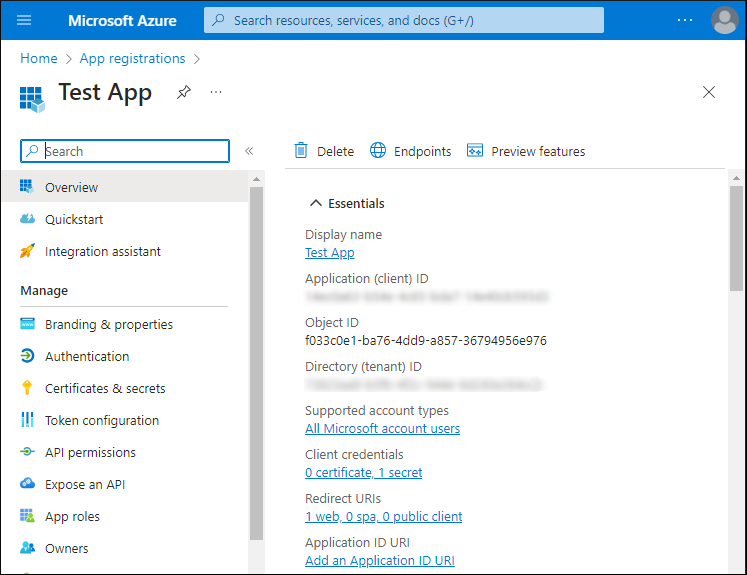
Click the application. The Overview page opens.
-
In the Overview page, take note of the following secrets: Application ID, Directory (tenant) ID, Client secret, Redirect URI. You will need these in a subsequent step.
-
In the SBS Console, run the
updateAppmutation and provide the previously obtained authorization details as parameters toAzureClientSecret.
For user authentication (that is, if you are using only the User Management Service), the only Azure secret you need is Application ID. The other secrets are required for the Email Service.
mutation updateAppAzure($id: ID!, $input: UpdateAppInput!) {
updateApp(id: $id, input: $input) {
azureClientSecret{
web {
application_id
}
}
}
}
Make sure to replace variables with the values mentioned in step 3 above.
{
"id":"YOUR_SBS_APP_ID",
"input": {
"azureClientSecret": {
"web": {
"tenant_id": "YOUR_AZURE_TENANT_ID",
"application_id": "YOUR_AZURE_APPLICATION_ID",
"client_secret": "YOUR_AZURE_CLIENT_SECRET",
"redirect_uri": "YOUR_AZURE_REDIRECT_URI"
}
}
}
}