OAuth 2.0 Service
The OAuth 2.0 Service provides means to programmatically authorize users with Google or Microsoft, for various business purposes that may be implemented in your application. For example, your application may allow users to send email managed by Google or Microsoft 365 providers directly from within the app.
Access info
| Endpoint | https://oauth-api.socrate.io/graphql |
| Required access keys | Tenant-level service access key |
| Pricing | Check the available purchase options. |
| Notes | To call the service, the access key must be provided in the x-api-key header of the HTTP request. If you are using the GraphQL console, you can view the service’s documentation and schema only after entering an access key. Make sure that the scope of the key allows access to the queries and mutations that you require. For example, to grant the key access to all queries and mutations, the key’s scope must be set to oauth-api:query:* oauth-api:mutation:*. |
Usage
Implementing OAuth 2.0 authorization with Google
To enable users of your app to connect their Google inbox to the app, the following prerequisites must be in place:
- From the Google Cloud Console (https://console.cloud.google.com/), you must create or update your Google project (Google app) so that it has support for Gmail API and OAuth 2.0 client credentials. For details, see Configure an OAuth 2.0 client in Google.
- Once you obtained your OAuth 2.0 credentials from Google, you must update the SBS app accordingly. For details, see Configure OAuth 2.0 for Google.
To authorize the user, you need to interact only with the SBS API (not directly with Google APIs). Note the following:
- The OAuth 2.0 access and refresh tokens obtained from Google as part of this process are stored by SBS and your app does not need to manage them at all.
- To perform the authorization, you will need to provide the internal user’s ID in your application (the so-called
approver) as input to thegenerateAuthorizationRequestmutation. Once the authorization process is complete, you will receive in the response anAuthorizationobject associated with that user ID. As long as the authorization exists, the user may perform the actions allowed by the authorization’s scope (such as sending email). - To view any of the previous authorizations, run the
authorizationsquery. - To revoke an authorization, run the
revokeAuthorizationmutation.
The following diagram illustrates the OAuth 2.0 authorization process from the SBS perspective:
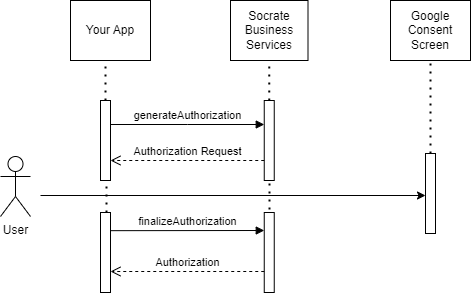
The process consists of the following steps:
- Run the
generateAuthorizationRequestmutation, for example:
mutation gen_auth_req($input: GenerateAuthorizationRequestInput!) {
generateAuthorizationRequest(input: $input) {
url
}
}
{
"input": {
"approver": "YOUR_USER_ID",
"provider": "GOOGLE",
"scope": ["EMAIL_SEND"]
}
}
- Redirect the user to the URL received in the previous step. The user will now see the consent screen, from where they can allow or deny access of your app to their Google account. If the user allows access, they are redirected to the
redirectUrlspecified in App settings. Note that the redirect URL contains an authorizationcodeandstateas query parameters, for example:

- Now that you have the authorization code, you can run the
finalizeAuthorizationmutation, for example:
mutation final_auth($input: FinalizeAuthorizationInput) {
finalizeAuthorization(input: $input) {
id
approver
provider
scope
createdAt
userInfo {
email
}
}
}
Make sure to populate input variables with the authorization state and code received in the previous step.
{
"input": {
"state": "YOUR_STATE",
"code": "YOUR_AUTHORIZATION_CODE"
}
}
You can now use the approver value (ID of the authorized user) in calls that require OAuth 2.0 authorization (such as the sendMessage mutation of the Email Service). For example, in the sendMessage mutation of the Email Service, one of the sub-fields of the from parameter is oauthApprover. When running this mutation, fill in this parameter value with the approver value used previously. For more information, see Sending email from a Google or Microsoft 365® email address.
Implementing OAuth 2.0 authorization with Microsoft
To enable users of your app to connect their Microsoft 365 inbox to the app, the following prerequisites must be in place:
- Your company must hold an Azure portal account (https://azure.microsoft.com) and be enrolled in the Microsoft Cloud Partner program (https://partner.microsoft.com). The latter ensures that users who give consent to your application to send email on their behalf will see a verified application publisher on the consent screen.
- On the Azure portal, you must create a new app registration so as to obtain the OAuth 2.0 client credentials required for performing on demand OAuth 2.0 authorizations. Also, your Azure application must have permissions to send email through the Microsoft Graph API. For details, see Configure an OAuth 2.0 client in Azure.
- The account that owns the Azure application must hold a Microsoft 365 Business Standard subscription.
- Once your app is configured in Azure, you must enter its OAuth 2.0 credentials (that is, client secret, client ID, directory ID, and redirect URI) into SBS. For details, see Configure OAuth 2.0 for Azure.
Otherwise, the implementation itself is exactly the same one as described above for Google. Namely, there are two steps to the authorization process:
- Run
generateAuthorizationRequest, in which you indicate (a) the ID of the user for whom authorization is requested, (ii) the scope of the authorization (currently, you can use EMAIL_SEND). The user is then redirected to the consent screen where they can grant authorization to your app for the requested scopes. When the user completes the authorization process, they are redirected to the configured redirect URI, which includes thecodeandstatequery parameters in the response. There is also a third response parameter calledsession_statewhich is currently not in use. - Using the obtained authorization
codeand thestate, runfinalizeAuthorizationto store the authorization for the given user. As long as the authorization exists, the respective user will be able to perform actions granted by the authorization scope.
To revoke existing authorizations, run revokeAuthorization.
Queries
authorizations
Lists previously created authorization records.
Arguments
| Argument | Type | Description |
|---|---|---|
| filter | AuthorizationsFilter |
Mandatory. Specifies the filter criteria to be used. See AuthorizationsFilter input. |
AuthorizationsFilter input
| Attribute | Type | Description |
|---|---|---|
| approver | ID! |
The internal user ID to which this authorization belongs. |
| scope | [Scope] |
Specifies the scope of the authorization. Valid values: EMAIL_SEND - filter only authorizations that have all scopes required to send email from SBS. |
Result
Authorization type
| Attribute | Type | Description |
|---|---|---|
| id | ID |
The unique identifier of the authorization record. |
| approver | ID |
The unique identifier of the user to which this authorization belongs. |
| provider | Provider |
Specifies the third-party provider from which this authorization was obtained. Valid values: GOOGLE, MICROSOFT. |
| scope | [Scope] |
Specifies the scope of the authorization. Possible values: EMAIL_SEND - this authorization has all scopes required to send email from SBS. |
| createdAt | DateTime |
The date and time when the authorization was created. |
| userInfo | UserInfo |
See the UserInfo type. |
UserInfo type
| Attribute | Type | Description |
|---|---|---|
EmailAddress |
The email address obtained from the third-party provider. |
version
Returns the API version.
Mutations
finalizeAuthorization
Finalizes an authorization request previously created through generateAuthorizationRequest. This is the second step towards obtaining the OAuth 2.0 access token from the third-party provider.
Arguments
| Argument | Type | Description |
|---|---|---|
| input | FinalizeAuthorizationInput! |
Provides input values to the mutation. See the FinalizeAuthorizationInput input. |
FinalizeAuthorizationInput input
| Attribute | Type | Description |
|---|---|---|
| state | String! |
Mandatory. Set this value to the state query parameter received in the url returned by generateAuthorizationRequest. |
| code | String! |
Mandatory. Set this value to the code query parameter received in the url returned by generateAuthorizationRequest. |
| redirect_uri | String |
Optional. If you provided a custom redirect URI when generating the authorization redirect, specify it in this input parameter as well. |
Result
See the Authorization type.
generateAuthorizationRequest
Generates an authorization request. This is the first step towards obtaining the OAuth 2.0 access token from the third-party provider.
Arguments
| Argument | Type | Description |
|---|---|---|
| input | GenerateAuthorizationRequestInput! |
Provides input values to the mutation. See the GenerateAuthorizationRequestInput input. |
GenerateAuthorizationRequestInput input
| Attribute | Type | Description |
|---|---|---|
| approver | ID! |
Mandatory. Specifies the user ID (in your application) for which the OAuth 2.0 authorization is to be obtained. |
| provider | Provider! |
Mandatory. Specifies the third-party provider from which the app password was obtained. Valid values: GOOGLE, MICROSOFT. |
| scope | [Scope!]! |
Mandatory. Specifies the scope of the authorization. Valid values: EMAIL_SEND - If you specify this value, SBS will request from the provider any scopes required to send email from SBS. This includes scopes that, from a provider perspective, may not appear as strictly required for email sending although such scopes are required in SBS, for example, reading of email metadata. |
| redirect_uri | String |
Optional. Lets you specify a custom redirect URI to which the user should be redirected after completing the OAuth 2.0 authorization process. |
Result
AuthorizationRequest type
| Attribute | Type | Description |
|---|---|---|
| url | Url |
Specifies the URL to which the user should be redirected in order to go through the OAuth 2.0 authorization process with the third-party provider. |
| state | String |
Specifies the state of the authorization. |
revokeAuthorization
Deletes a previously created authorization. The outcome is that the user ID to which this authorization belongs will no longer be able to perform actions within the scope granted by the authorization.
Arguments
| Argument | Type | Description |
|---|---|---|
| input | RevokeAuthorizationInput! |
Provides input values to the mutation. See the RevokeAuthorizationInput input. |
RevokeAuthorizationInput input
| Attribute | Type | Description |
|---|---|---|
| id | ID! |
Mandatory. Set this to the ID of the authorization that is to be revoked. |
| approver | ID! |
Mandatory. Set this to the user ID for which the OAuth 2.0 authorization is to be revoked. |
Result
RevokedAuthorization type
| Attribute | Type | Description |
|---|---|---|
| id | ID |
The unique identifier of the authorization record. |
| approver | ID |
The unique identifier of the user to which this authorization belongs. |
| provider | Provider |
Specifies the third-party provider from which this authorization was obtained. Valid values: GOOGLE, MICROSOFT. |
| scope | [Scope] |
Specifies the scope of the authorization. Possible values: EMAIL_SEND - this authorization has all scopes required to send email from SBS. |
| createdAt | DateTime |
The date and time when the authorization was created. |